It’s common for our computers to experience occassional lags and performance slowdowns, especially when many apps or programs are running. This can even cause the device to heat up. But what if there are no apps open and it’s still lagging? You might want to check if your machine is infected with crypto-malware. Cybercriminals could be secretly using your computer for mining cryptocurrencies without your authorization. This activity can deteriorate your system’s performance, increase electricity costs, and might even damage your hardware.
Chainalysis reports state that the payments for crypto-malware attacks hit over $1 billion. This highlights the urgent need for learning, detecting, and protecting against such threats. The next sections of this article will go deeper into explanations of how crypto-malware works, some of the interesting case studies in crypto-malware, and a number of effective defense strategies.
What is crypto malware?
Cryptomining malware, also known as crypto-malware, is just malicious software that uses the computer resources of a victim to mine digital currencies like Bitcoin automatically. In contrast, for instance, to ransomware that encrypts files and demands payment, the operation of this malware is carried out secretly. It will use a victim’s processing power to do all the heavy work involved in mining digital currencies.
Most typically, such malware is spread by deceptive means, such as phishing emails, clickbait, and insecure websites. The moment it infects a system, it starts to hijack its CPU or GPU for the mining process. Some of the signs include a noticeable slowdown in system performance, increased electricity bills, and the system running warmer. It’s these symptoms that lead to investigations and ultimately result in the discovery of the crypto-malware.
A number of recent studies highlight the growing trend of this malicious activity. For instance, a Comparitech report mentions a 399% growth in cryptojacking for the year 2023. This activity has reached prolific proportions with the increase in cryptocurrency value and the comparatively low risk to cybercriminals. Cryptojacking is a stealth operation; a normal user cannot immediately know that it is happening to them.
Crypto malware vs. ransomware
Crypto malware and crypto-ransomware are two types of malware that differ in the objectives for their actions. Whereas both are exploiting victim systems, the methods and end goals show remarkable differences:
Crypto malware
- Highjacks computational power to mine cryptocurrency.
- Aims to stay under the radar for as long as possible.
- Steals system performance and causes an increase in electricity consumption.
Crypto ransomware
- Encrypts the files of the victim and requires a ransom to decrypt them back.
- Confronts the victim directly, usually causing immediate disruption.
- This is meant to ensure instant payment by the victim.
Knowing how these differ should enable a proper defense against such threats. Crypto-malware is more on hitting stealthy and hijacking resources for a long time, whereas ransomware hits very hard and fast, enforcing instant action on its victims. Both, however, pose serious risks to people’s finances and operations in terms of threats.
Worth noting, however, is that most of the strategies cybercriminals use to deploy these malware types are similar. For example, both are known to originate from phishing emails and even from compromised websites. Hence, a holistic strategy in cybersecurity has to deal with them cohesively.
How do crypto malware attacks work?
Most crypto malware attacks flow from vectors such as:
- Phishing emails
- Malicious websites
- Software vulnerability exploits
After infecting a system, this malware helps attackers mine cryptocurrencies by hijacking the processing power of the computer, leading to a slow performance while at the same time increasing electricity consumption. In this way, the attack is hard to detect and hence very dangerous. The attacks target devices with high-performance hardware to maximize the output of mining, laying a great burden on computer components.
Most of the time, users are exposed to crypto-malware through very alluring phishing emails or through infected ad networks serving malicious code. The computationally intensive process of crypto mining brings down the performance and reduces operational efficiency with added operational cost. Since a single infected network brings decent returns to attackers, the need to have comprehensive defense mechanisms and raise awareness among users has been strongly realized. Quality antivirus software is important in detecting it early to mitigate its actions, hence avoiding large-scale damage and financial loss.
Examples of crypto-malware attacks
Several very well-documented and recent crypto malware ransomware attacks have demonstrated both the severity and the ingenuity of such threats. The following are a few examples:
Prometei
Prometei is a botnet that uses vulnerabilities in Microsoft Exchange to mine Monero. It has hit a number of companies all over North America and Europe silently hijacking their systems for cryptomining. Herewith, this botnet not only mines cryptocurrency but it also infiltrates sensitive data from infected systems posing a dual threat.
PowerGhost
PowerGhost uses spear-phishing as the initial infection vector and spreads itself through Windows Management Instrumentation and EternalBlue. It is able to disable antivirus software to enhance its mining activities. With this, it extends the lifetime of infection while being concealed from classic defenses, ensuring maximum profits for the operators.
Graboid
Graboid is the very first cryptojacking worm that spreads via Docker Engine, targeting unsecured Docker daemons. Secondly, it installs a Docker image for Monero mining and affects systems worldwide. This example shows the dangers of misconfigured or unsecured cloud infrastructure.
WannaCry ransomware
This ransomware encrypts user data and demands payment in Bitcoin for decryption. Leveraging the EternalBlue vulnerability—already plaguing systems around the world—WannaCry once again underlined how highly destructive ransomware-crypto malware hybrids have been. The attack inflicted heavy financial and operational damages to both public and private sectors alike.
CryptoLocker
Another variant of ransomware is CryptoLocker. It attacks, keeping cryptocurrencies in mind, and encrypts files, demanding ransom in digital currency. This has become a huge event for disruption in activities and financial losses. The far-reaching extent of CryptoLocker showed how effective the social engineering methods of spreading malware, like phishing, could be.
Coinhive
Coinhive enabled websites to embed a JavaScript miner that utilized the CPU of visitors. Developed initially as a new revenue stream, it turned quickly into a tool for malicious cryptojacking. In this respect, the ease by which Coinhive’s script could be embedded in websites without visitors’ knowledge set a clear case for vigilant web security.
XMRig
XMRig is an open-source crypto mining software usually repurposed for malicious crypto mining. It has been incorporated into quite a number of malware types for the surreptitious mining of Monero. Cybercriminals often bundle XMRig with other kinds of malware to form multifunctional threats that are much harder to neutralize.
Darkgate
Darkgate is multifunctional malware that includes crypto mining, ransomware, and credential stealing. Primarily, it gives its assault towards Windows systems—no doubt, all-round and perilous. In this way, its loaded functionalities make it one single tool for cybercriminals with the capability of causing enormous damage and disruption.
How to defend against crypto-malware attacks
Basically, defending from crypto-malware involves a multi-faceted approach, both by the use of technology as well as user awareness. Here are some effective strategies of defense:
- Install ad-blockers and anti-crypto mining extensions: Tools such as ad-blockers and specific anti-mining extensions can block malicious scripts from running on your browser.
- Keep software up-to-date: Regularly update your operating system, browsers, and plugins to patch known vulnerabilities that malware can exploit.
- Use reputable antivirus software: Run antivirus software with real-time scanning and malware detection.
Be careful of malicious links and suspicious sites: Be wary of suspicious emails because they might contain phishing emails or clickbait. Tools like WOT’s Safe Browsing feature enable a user to analyze a link before clicking on it as to whether it is safe or not.
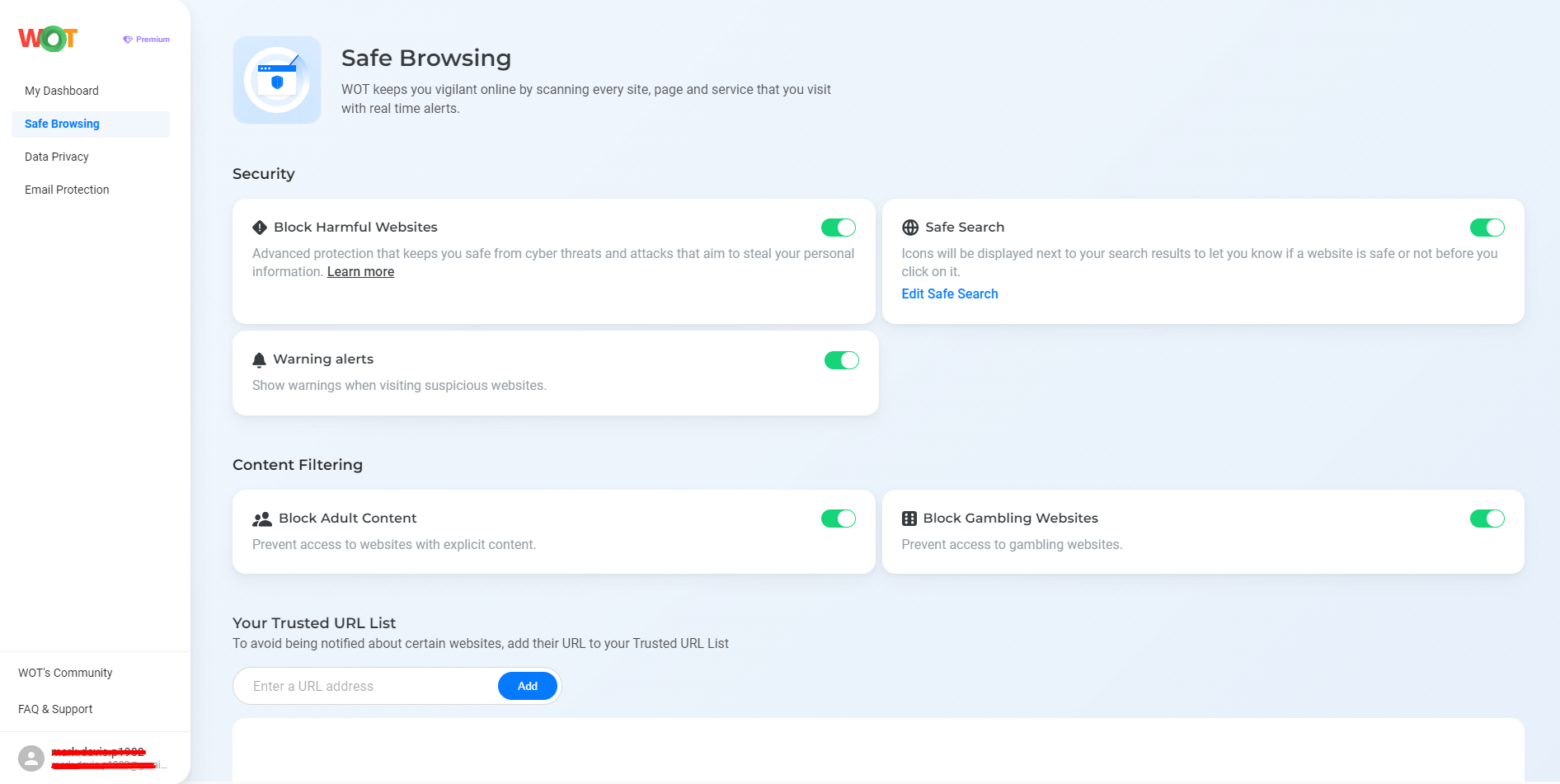
- Disable JavaScript for unknown sites: Most cryptojacking scripts are forestalled when JavaScript is disabled.
- Do regular backups: Back up your data regularly to minimize the harm in case of a ransomware infection or other forms of destructive malware.
With these safeguards in place, you can significantly minimize the risk of becoming a victim of these online scams. Keeping up-to-date on the latest threats, users at intervals should review their security practices for maximum protection of their devices and private information.
Protect your devices from crypto-malware
Though crypto-malware is a threat that will never die, it will keep evolving. Therefore, it’s every internet user’s duty to always be vigilant and proactive. Take charge of your browsing experience through security tools and best practices that work to protect your devices.
Get started now! These protective measures are put in place to help you navigate safely online.
FAQs
What is the most common symptom or indication of crypto-malware infection?
The most common indication is very high usage on the CPU, which causes the system to become really slow and overheat. You can check it using your computer’s task manager or activity monitor.
Can software updates protect against crypto-malware?
Yes, keeping your software updated with the latest security patches and updates will patch vulnerabilities that malware might exploit.
How would I know a link is safe to click?
It’s important to learn how to know if a link is safe. Before clicking a link, use tools like WOT’s safe browsing feature to check if it’s legit. Avoid links in unsolicited emails and other messages.
How can I protect myself if I think my device is infected with crypto-malware?
Disconnect from the internet, run a complete antivirus scan, and then remove threats it detects. Also, never forget to change all your passwords and take into consideration activating two-factor authentication.
Are any types of devices more vulnerable to crypto-malware?
While anything connected to the Internet may present a target, out-of-date software, weak passwords, or no security at all significantly contribute to its vulnerability. Be sure to have strong security practices across all devices at all times.
