Malware is a massive threat to individuals and organizations. Deliberately intrusive, often invisible, and capable of causing serious damage, it’s a constant risk, stealing private information from individuals and bringing businesses across sectors to their knees. In this guide, we’ll not only provide a malware definition but also explain what it is, how it works, how it’s able to infiltrate our computers, and what measures we can take to protect ourselves and our computer systems from attack. Whether you’re an individual user, with one or two devices to look after, or a manager responsible for the security of dozens or even thousands of computers in an enterprise structure, knowing more about malware will help you to introduce better security.
What is malware?
The term malware refers to a variety of harmful computer software aimed at breaching and harming the user systems. Such software can attack a device in many different ways, such as viruses, worms or trojans, ransomware, spyware, or others. Although the different sorts of malware have various characteristics, they usually have one common purpose: destroying computer security and making user systems unusable.
Malware is aimed at compromising your device, getting at your data, or otherwise damaging you. The word itself is a portmanteau of ‘malicious’ and ‘software’, a blanket term that covers a vast array of various bits that will find their way into your systems, sneak past your defenses, and wreak all kinds of havoc. There are many different kinds and they show up in different ways, but they often appear seemingly out of nowhere to keep you up at night as they clog your systems and swipe your data.
How does malware get on your computer
It’s important to understand these methods of infiltration. After all, prevention is the best cure. Malware can break into your devices using several methods, and each targets the malware to a different vulnerability. Here are the top ways in which malware can infect your systems; each method opens doors to risks.
Phishing attacks
These are fake emails or messages that try to get you to click on malicious links or files. Cybercriminals disguise them to look like legitimate emails. Phishing attacks soared to 58.2% in 2023 based on a report from Zscaler.
Infected websites
Visiting malicious or compromised sites can lead to ‘drive-by downloads’, when you are sneakily installed with malware. Ad networks, too, can be culprits: malicious ads can appear on legitimate sites, and you can end up downloading with no intention of doing so.
Removable drives
Malicious software can be transmitted to your system via USB sticks or external hard drives that include malware and transfer the problem when connected to your system. The risk is higher especially when multiple systems and drives are shared in a corporate environment.
Software from unreliable sources
Downloading and installing software from third-party sites will typically come with some kind of malware or other potentially unwanted program, so you should always be downloading from a source that is verifiable and trusted, rather than from anywhere else.
Obfuscation techniques
Polymorphic and fileless malware are another way to hide evidence of the malware, by changing its appearance and stepping around security controls, to some extent. These variants change the code of a malware significantly to evade detection.
Types of malware
Grasping the different kinds of malware makes recognition and responses to such threats much easier, as each kind of malware works in different ways to perform its designated task, which enables you to implement countermeasures. It is important that you are aware of these categories of malware.
Below are the main malware types and the reasons why they are considered a danger:
Viruses
A virus attaches itself to files, and each time it is executed it reproduces itself and spreads further. Ultimately, its goal is to spread and cause damage, either by infecting other systems, by directly damaging data, corrupting files, or indirectly by consuming all the system resources available. The most common way that a virus spreads is via email attachments or downloads from an infected website.
Worms
These are self-replicating viruses that spread from computer to computer, often causing network instability and data corruption. Unlike viruses, worms don’t need a host file and can spread on their own. That makes worms especially virulent in network environments, where they can spread quickly.
Trojans
Masquerading as legitimate software, they trigger malicious functions upon execution. Trojans are especially treacherous if they create a backdoor in a system through which other malware can pass. They can be concealed within seemingly innocuous software leading to severe security breaches.
Spyware
This type works in the background, without your knowledge, gathering any private data, such as passwords and private information you may supply. It is then sent to the attacker to be used at their discretion. Spyware can be used in corporate espionage and for identity theft and data theft.
Ransomware
Ransomware encrypts data and asks that a ransom be paid to get it back. Ransomware increasingly cripples people and organizations. As with the WannaCry and Petya ransomware attacks in late May and June 2017, the impacts can be massive and global. Ransomware has even crippled hospitals.
Adware
As the name implies, it hosts and delivers irrelevant adverts, and it can track your browsing history. It’s less destructive than a virus, but it could cause privacy problems and slow down your system. Adware can flood your browser with pop-ups and other graphics and can disrupt your browsing.
Rootkits
Because they provide unauthorized access and control, rootkits are hard to detect and eliminate. Rootkits tend to grant the newest malware the highest level of system access, known as administrative privileges. This gives rootkits the ability to manipulate deep within a system. Unsurprisingly, because of this deep access, it is one of the most challenging forms of malware to remove wholly.
What can malware do to your computer?
There are several items on your computer that malware will specifically go after to damage data, performance, and security. These threats can range in severity from minor annoyances to major systems failures. Here is what happens to your computer when it has malware.
Data theft
Malware can extract sensitive data such as passwords, card details, and personal information, resulting in identity theft and financial losses. Stolen data can be sold on the dark web or can be used for direct monetary gains.
Service disruption
Ransomware and other kinds of malware can encrypt systems so users can’t access them, shut down services, and hold organizations’ most valuable data hostage. In worst-case scenarios, operations shut down entirely for days, weeks, or longer. This costs businesses money and time.
System damage
For the victim of such malware as worms, for instance, system files might become corrupted, data deleted, and/or various system settings changed in a way that makes the system less stable or even unusable. The endeavor of recovery is often costly, and there’s the likelihood of the loss of data as well.
Resource hijacking
Malware can also use your system’s resources for tasks such as sending spam emails, running botnets, or crypto mining, thus making your device slow and wasting your electricity. Cryptomining malware not only significantly decreases the performance and even the lifespan of your hardware, but it also generates a lot of unnecessary heat.
Espionage
Some spyware can record your activities, log your keystrokes, get into your webcam, and take screenshots from your computer without your knowledge. In the most extreme instances, this type of spying can result in personal or corporate data leaks.
How can I tell if my device has malware?
Malware can infect both computers and mobile phones, posing significant threats to your device’s security. Recognizing the signs of a malware infection early is crucial to preventing further damage. Whether you’re using a computer or a mobile phone, being vigilant about the following symptoms can help you protect your device.
Unexplained data usage
A sudden spike in data usage (Will usually be more noticeable on your phone) could be a sign that malicious software is using your device to send data to remote servers without your knowledge. This might lead to unexpectedly large bills, slower internet speeds, and potential data overcharging, affecting your connectivity and finances.
Rapid battery drain
Malware often runs background processes that consume significant battery power. If your device’s battery is draining quickly, even when it’s not in heavy use, malware could be the culprit, potentially shortening the lifespan of your device.
Unauthorized messages
Malware can take control of your texting and messaging apps, sending spam links or messages to your contacts without your knowledge. If friends or colleagues report receiving strange or suspicious messages from you, it could be a sign that your device is infected.
Performance issues
Infected devices can become sluggish, crash frequently, or have software or apps that take longer to load than usual. These symptoms may indicate that malware is interfering with your device’s normal operations, making it slower and harder to use.
Unfamiliar apps
Malware can install software and apps on your device without your consent. These might appear to be helpful, but they often serve as fronts for malicious software. If you notice apps on your device that you don’t remember installing, it’s a strong indication that your device may be compromised by malware.
Protect yourself against malware
Stopping malware before it becomes a problem is the best way to protect your devices. By incorporating some common sense and the use of the proper tools, you can substantially lower your risk. Here are some practical steps you can take to protect your systems:
Use WOT’s Safe Browsing feature
If you are worried about malware, you can turn on WOT’s Safe Browsing feature. This feature will warn you if a site you are about to visit contains malware or is otherwise dangerous.
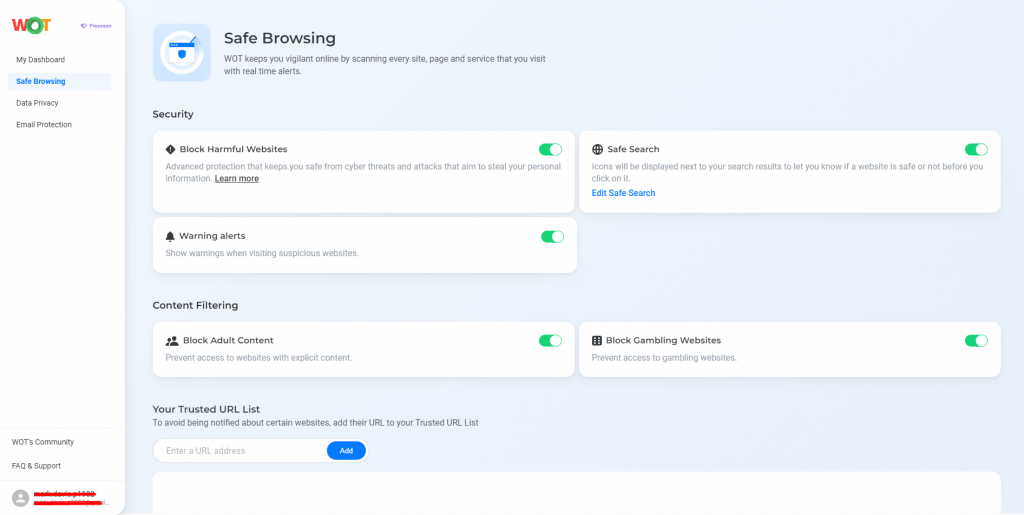
By keeping you away from potentially dangerous sites, your computer is safe from the damage that malware can introduce.
Install reliable security software
Use antivirus and anti-malware programs that combine real-time protection and regular updating.
Avoid suspicious downloads
Download software and files only from sources that you trust.
Use strong passwords
Generate unique, strong passwords for your accounts; turn on multi-factor authentication where you can. Use a password manager to manage them.
Update software regularly
Make sure your operating system, applications, and security software are all up to date – that way, you will be protected against known flaws and vulnerabilities. Regular updates will typically plug security holes that malware can take advantage of.
Be wary of email attachments
Do not open email attachments or click a link in a suspicious or unknown email. Using the same technique as the spear phisher, the malicious link may appear to be coming from someone you know and trust, even when they have been compromised. Check with the sender to verify before opening any attachments or clicking a link.
A secure digital future
Malware is a real threat to the assets on your device – so, commit to protect them against malicious software: be vigilant, be informed, and take action against malware. Use WOT – and other tools – to help ensure a safer internet experience, protect your information, and maintain a secure cyber world.
FAQs
Is malware only an issue for Windows users?
No, the problem concerns any operating system, be it Windows, macOS, Linux or the Android or iOS family of mobile operating systems on smartphones.
Can antivirus software detect all types of malware?
Although antivirus software can identify most types of malware through a series of signals (files and programs that are infected), it is impossible that it will manage to capture each and every single virus. Regular updates are necessary to avoid exposing the computer to potential threats.
What should I do if I suspect my device is infected with malware?
Unplug from the internet, run a full system scan with reputable anti-virus software, and delete any detected threats. Seek professional help if the problem lingers.
How often should I update my security software?
It is always good practice to install security applications as soon as they are available. System and application updates give your system protection against newly developed threats.
Are free antivirus programs effective?
While free antivirus programs usually suffice to provide basic protection against common threats, many only improve their features in their premium versions, which deserve to be considered by users who want enhanced protection.
