You sip on your first cup of coffee, ready to get into a full schedule of tasks, when suddenly your computer screen goes black. A message demands a ransom in Bitcoin to access your files. For many remote workers, this alarming scenario is all too common as cyber threats become more sophisticated. In fact, according to a report by Alliance Virtual Offices, home workers have been a target since the onset of the pandemic, with 238% in volume on cyber attacks.
While telecommuting allows many things to become flexible and easy, this also opens up a host of associated cybersecurity challenges that cannot be ignored. The requirement for strong online security measures has never been more pressing.
What started as a gradual shift from office spaces to home offices accelerated at an unprecedented rate—one that outpaced even the most positive projections as present world events and shifting workplace trends took hold. This places both personal and company-based interests in a more vulnerable position to cyber-attacks.
Home networks, which are normally the first line of defense for most remote workers, lack the security protocols one might find in traditional office settings. This places every remote worker in a situation whereby understanding the risks and working to counteract them is of prime necessity. Cybersecurity is not just about information protection; rather, it is a matter of personal and professional integrity.
One assumption that can prove dangerous is: working from home provides a haven safe from cyber threats. Without structured IT environments, such as those found in offices, the remote worker is exposed to various vulnerabilities. Web of Trust comes in handy in this respect, as it provides safe browsing, data breach monitoring, and many other facilities designed for remote work situations. You could significantly enhance your defenses against cyberattacks if you utilize web security tools like WOT, where most of your work-from-home activities could be much safer.
Security risks of working from home
There has been an increase in security issues with working remotely. Usually, the safe measures available in the office setting are absent for remote workers. In this change, many opportunities are created for several kinds of cyber threats to attack and hamper your workflow by revealing sensitive data:
Phishing and social engineering attacks
Phishing emails are misleading messages that are supposed to entice users to give away personal information. They can appear as if sent from genuine sources, and it is, therefore, very hard to identify them.
Social engineering is the manipulation of people to conduct specified actions or give away classified information and one of the most common methods is called vishing. Remote work has increased the reliance on emails, hence increasing such an attack. Always be suspicious of unsolicited and suspicious emails. Check the sender’s information carefully.
File sharing
Sharing files, especially across unsecured platforms, is highly risky. Malicious files could enter your system and steal your data. One needs to think carefully about secure mechanisms of file sharing.
End-to-end-encrypted tools take a safer route for the transfer of sensitive files. From time to time, audit the files and permissions shared so that at any point in time, unauthorized access is minimized.
Ransomware
Ransomware attacks lock users’ files and demand money to unlock them. This can ultimately bring your work to a dead end. The question here is to take a proactive stance to avoid becoming a victim.
Regular backups and up-to-date antivirus software are major defenses against such attacks. Paying the ransom does not guarantee recovery of data and only encourages more criminal activity.
Weak passwords
One of the easiest ways hackers gain access is through weak passwords. Easy or repeated passwords make it only more susceptible to unauthorized access.
Strong, unique passwords are needed. Use a mix of upper and lowercase letters, numbers, and special characters. A password manager can help a lot in creating complex passwords and storing them safely.
Read more: How Long Will It Take to Crack My Password?
Unsecured WiFi networks
You also expose yourself to threats of data interception and hacking by using public Wi-Fi networks, which are mostly unsecure. Only access secured networks with WPA2 protection in place.
Change the default password on your router, and regularly update its firmware to be more secure. And when using public WiFi, log in via a trustworthy VPN for added protection.
Expanded attack surfaces
Remote work increases devices and networks that require protection. Each device serves as another potential port of entry for cyber threats. That is where comprehensive measures for security help in managing these expanded attack surfaces.
Security endpoint solutions monitor and secure all network devices. Updates to security protocols—enacted regularly—help adapt to new threats.
11 Security tips for employees working from home
Safety involves taking multiple security measures while working from home. Here is your work from home security checklist:
Ensure WiFi security
Securing your WiFi has to do with making a change in the default settings of your router and creating strong, unique passwords. WOT’s WiFi scanning feature on Android allows users to track unsecured networks with additional security insights.
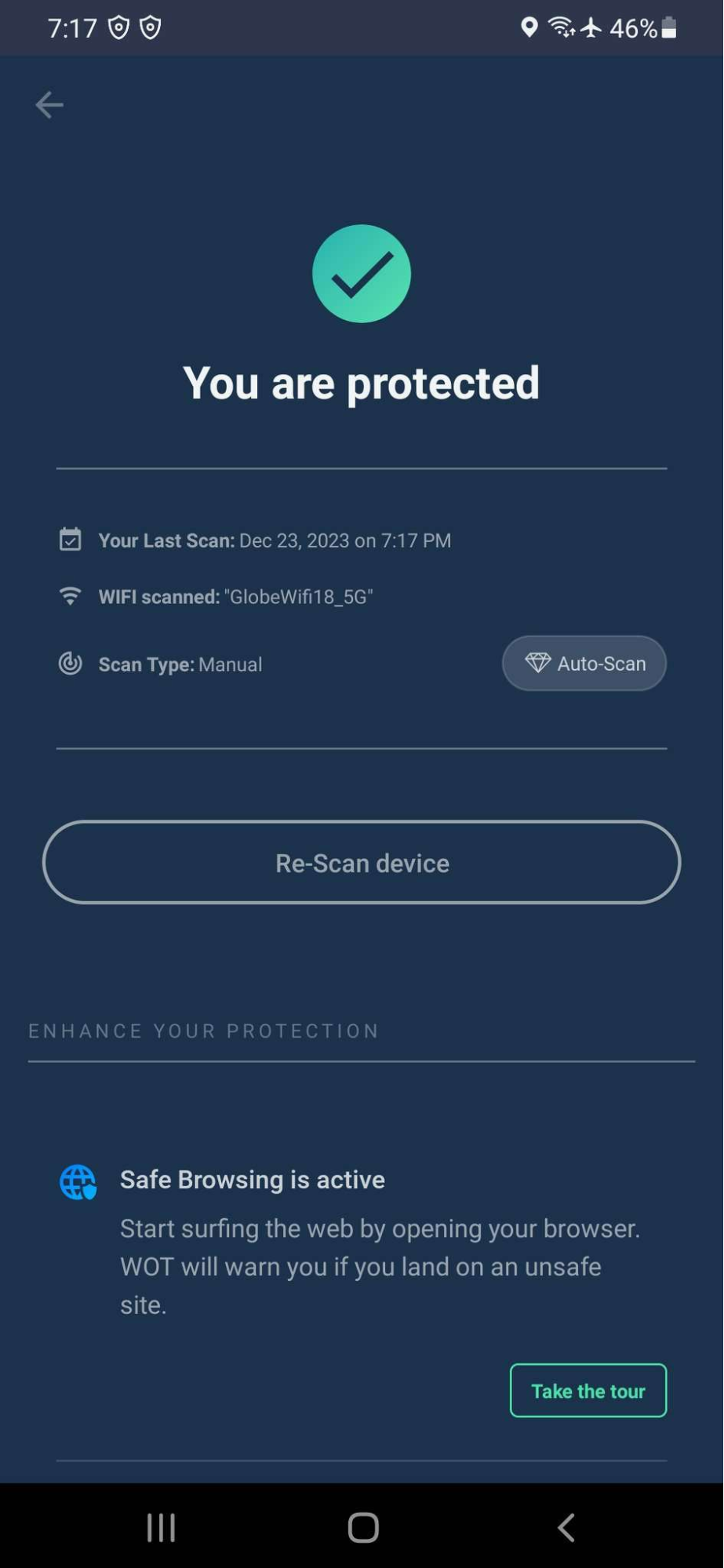
You should also perform regular checks on your WiFi network for suspicious activities. You could create a guest network for visitors that will improve the security of your main network.
Avoid phishing attacks
Get protected against phishing attacks with WOT’s features. With the Safe Browsing feature, you get protected from visiting rogue sites, so that you can have a secure experience while online.
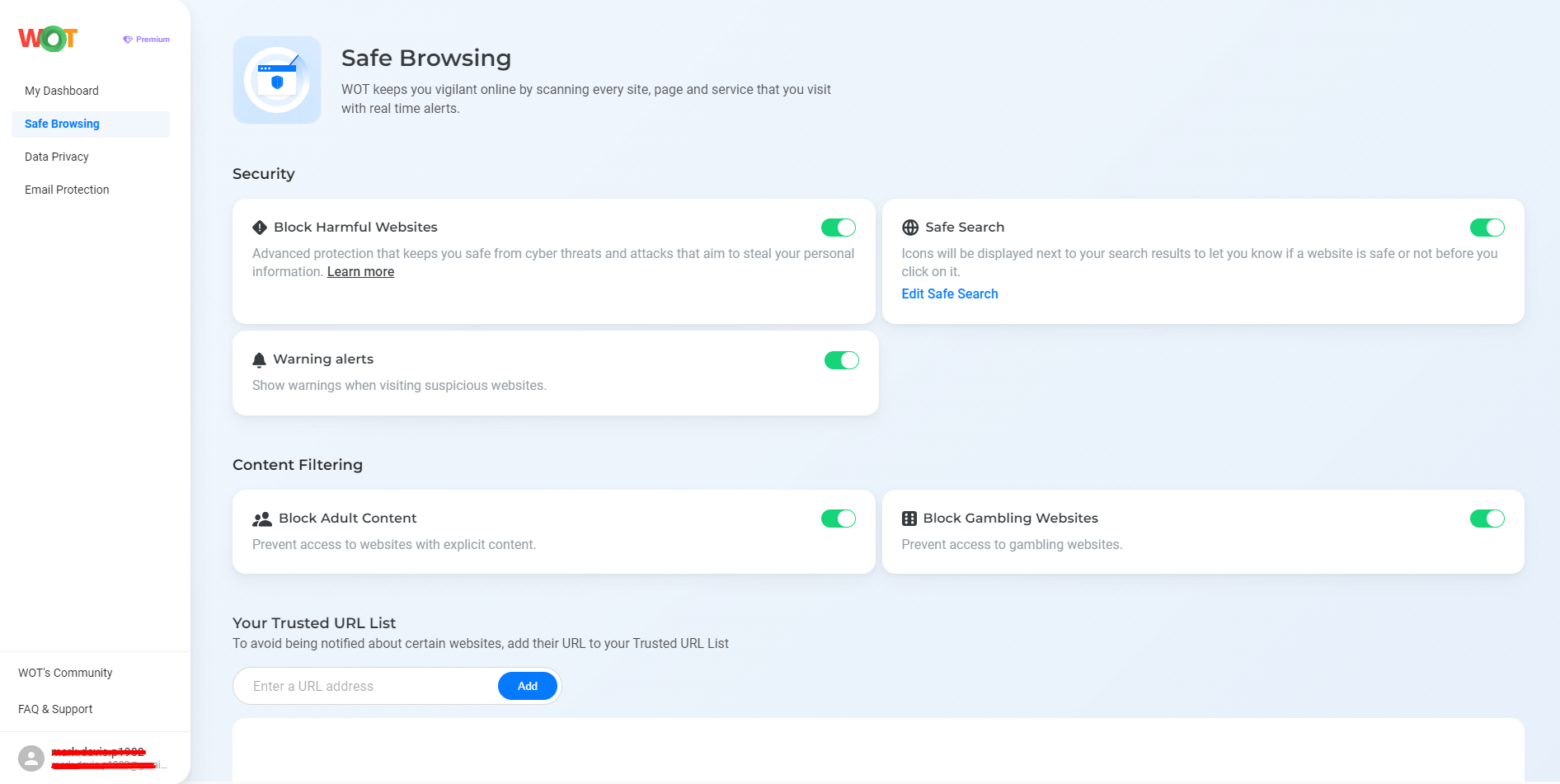
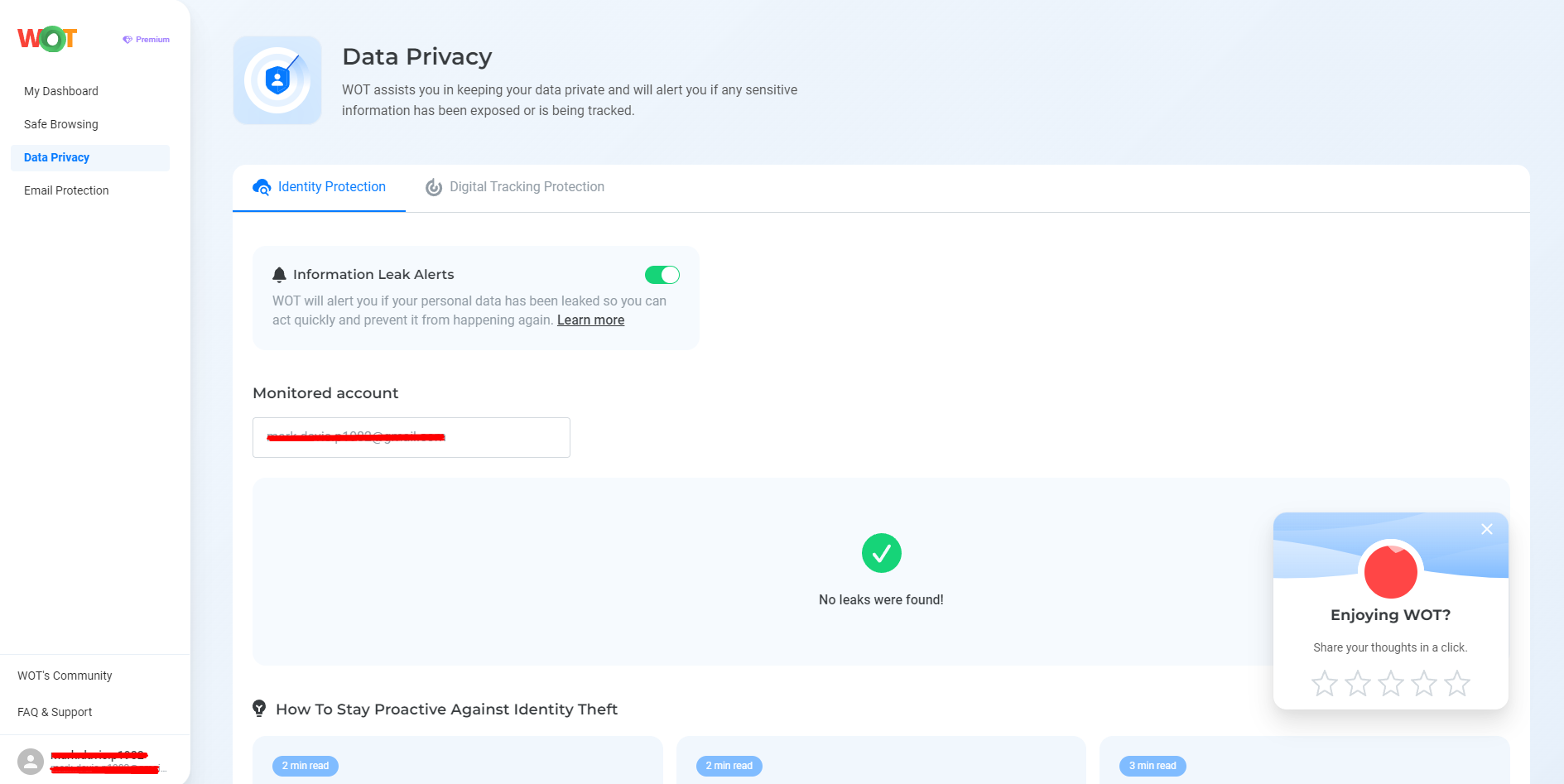
The Data Privacy feature protects your identity by warning you in case of leakage of any personal information, including passwords.
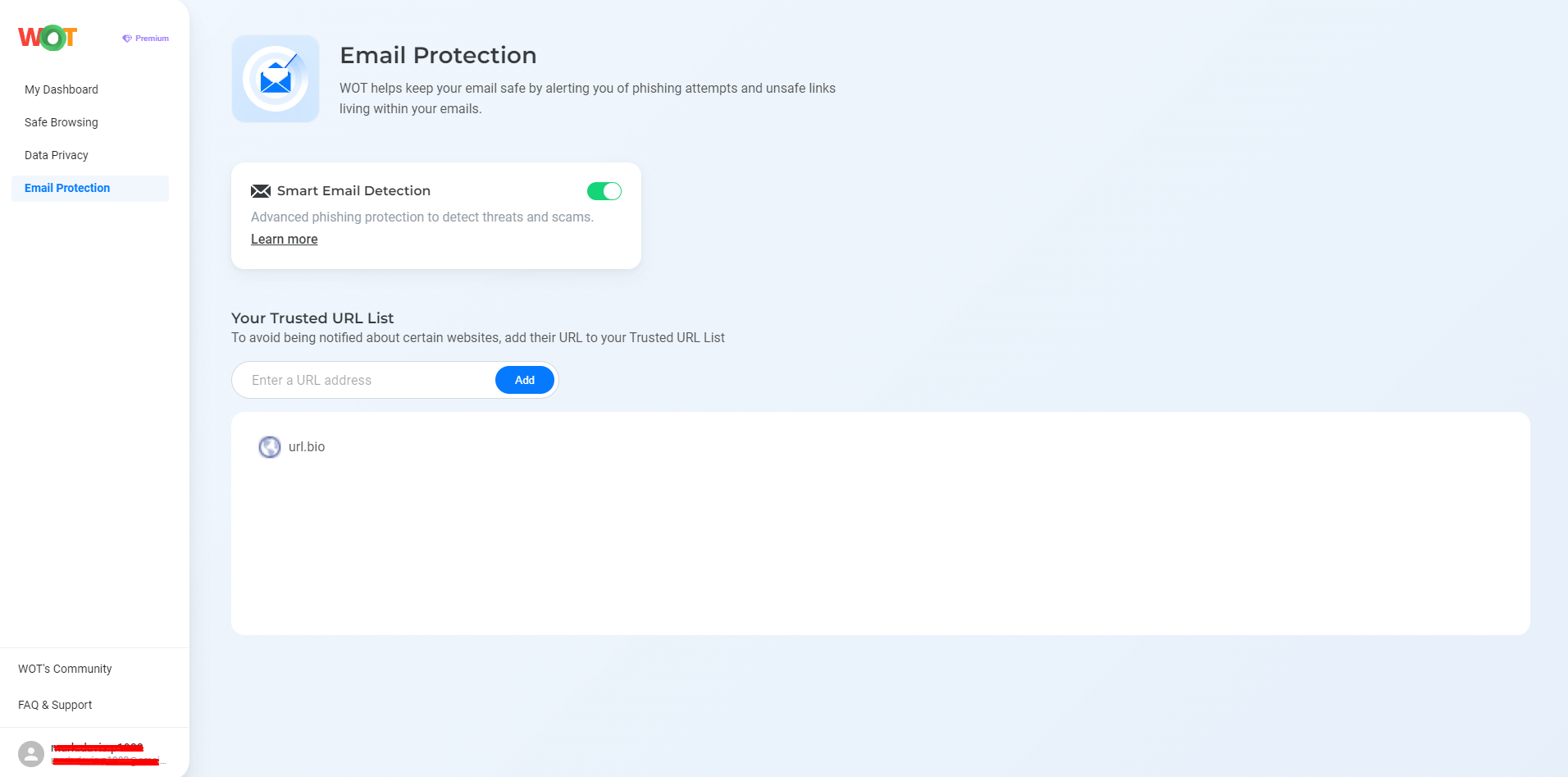
The Email Protection tool safeguards your email by detecting and blocking phishing and malicious links.
Create strong passwords
One of the remote work security best practices includes using unique and complex passwords for each of your accounts. Try not to use any personal information or common phrases. The passwords should be at least 12 characters long with both uppercase and lowercase letters, numbers, and at least one special character.
All these measures will make life very hard for cybercriminals in an attempt to crack your password. Of course, such risks can also be reduced by updating regularly.
Use 2-factor authentication
Enable 2-factor authentication on every important account you can. This will add a step to the process of access and require a second form of verification besides just a password.
2FA drastically reduces the risks of unauthorized access in case someone manages to guess or hack your password. Biometric verification through fingerprint or facial recognition is a safe secondary method.
Install antivirus software
Install antivirus software on the device that will provide complete security. The regular update run protects the device against more recent threats. Useful antivirus software will identify and neutralize malware before major damage is done.
Scheduled scans can expose and remove hidden threats. A reputable antivirus provider will have a system to keep you protected against known and emerging threats.
Use a VPN
A VPN encrypts your Internet connection, providing privacy and security beneficial to those working on company resources from home or using public Wi-Fi. It will keep you safe while the VPN is on during work hours.
Another advantage of a VPN is that it will prevent your ISP from monitoring your activities, thus safeguarding all of your online activities better.
Separate work and personal devices
Use different devices for work and personal activities to reduce the risk in case one is compromised. Separating work and personal data makes it easier to manage and implement security protocols.
Regular auditing of the software installed in work devices ensures adherence to the security policies while preventing cross-contamination as well.
Secure file sharing
Share files on secure and encrypted platforms rather than sharing sensitive information over an unsecured channel. Be sure to double-check the recipient details before sharing. Employee education on safe file sharing minimizes the risks of a breach.
Keep your operating systems and software up-to-date
Patching known vulnerabilities regularly considerably improves system security. Make sure to turn auto-update on to guarantee protection against a newly discovered threat at all times.
Not updating your software exposes your system to known exploits so develop a habit of checking for updates on all installed software at regular intervals, and this will always keep you on the most secure versions.
Use strong passwords for your devices
Set a unique and strong password for all devices used in the work environment. This creates another layer of protection that guarantees better security against unauthorized access. Keep your device locked whenever you are not using it and enable biometric verification if the setting is available.
Tip: A mix of device passwords and multifactor authentication is the highest level of protection.
Use a password manager
They generate and store complex passwords securely, so you won’t need to remember many different passwords. LastPass and Bitwarden are basically feature-rich tools that turn them into applications of great utility.
Reliable password managers warn you about possible security breaches and suggest stronger ones whenever necessary.
Level up your remote work security
These work-from-home security tips, when implemented, will significantly minimize your cyber risk. The measures described herein offer maximum protection for remote workers. Robust tools will help in easily securing one’s online activities. Get to implementing these practices today and avoid the subtle chances of losing your data.
Remember: Cybersecurity is a continuous process. Vigilance can keep a remote work environment secure by keeping one informed of new threats and thus tailoring your practice to them. Keep in mind that your proactive approach will not only protect your data but also assure you of being more productive while working from home with much less stress.
A safe work environment is a productive environment. Be sure to act now and keep the integrity of your remote work setup. It is time and effort well spent setting up and having good security in place to bring about peace of mind and protection.
FAQs
What should I do if I suspect my device has been compromised?
In case you suspect that you have been breached, disconnect the device from the internet immediately. After that, run a full antivirus scan, change your passwords, and contact your IT department or provider for any assistance you may need further on the above. This will facilitate the containing of this threat to avoid further destruction. Take notes of all activities that appear very suspicious and submit these to the appropriate authorities to help in the investigation.
How can I make my video-conferencing sessions secure?
Safeguard video conferences with end-to-end encrypted platforms. Set up a password for the meeting, give access from the waiting room only to the people who are supposed to attend it, and update software regularly to avoid security vulnerabilities. This can be achieved by reviewing the settings of the meetings every now and then such that it covers or allows access to intended persons only. Ensuring education about secure video conferencing practices among all attendees may prevent potential breaches.
Are there any specific tools recommended for secure remote work?
Highly recommended are tools such as LastPass for the best password management and Bitdefender for the highest antivirus protection. These two tools can be helpful in giving added features to further enhance your security while working remotely. In combination, the tools give layered security, significantly dropping the risk of cyber threats.
What is the best way to handle sensitive information while working from home?
Make it a policy to share confidential data using encrypted comms. Regularly back up data on secure storage solutions and avoid sharing critical details through insecure channels. Consider using an encrypted mailing service and secure cloud storage for additional safety. Strict access controls ensure that sensitive data is only accessed by authorized personnel.
How can I educate myself further on remote work security?
Keep current with the latest best practices in security through leading blogs with cybersecurity tips for remote workers and other information outlets. Take online classes and webinars. Membership with cybersecurity professional associations is worthwhile for acquiring new information and deriving best practices. Approach new information with curiosity to enhance preparedness and understanding of cybersecurity.
